PIs have the responsibility of ensuring that data collected for research meets regulatory as well as UMBC data use requirements to protect human subject research data in addition to safeguarding participants from risks and harms. Storage mediums range from laptops/tablets to external devices (e.g., memory stick) to shared electronic filing systems. Each has challenges for size of storage and location (filing cabinet, locked lab) but also for protection and security.
PIs are also responsible for ensuring that data stored follows what they state in an application to the IRB and is not intentionally or unintentionally disclosed to unauthorized parties. They also must follow UMBC’s policies and guidelines that govern general campus computer use.
Please review the extracted information from the UMBC Department of Information Technology (DoIT) Data Use Guidelines (last modified 5/5/2020) and access your Kuali protocols dashboard to create an application describing the use of secondary use of data. The OPRC has created a Kuali Protocol User Guide to assist you in creating a protocol. Data Use Agreements (DUA) may also be required; see the Office of Sponsored Programs DUA page for additional information.
The IRB recommends PIs obtain specific information on the steps to take to protect sensitive data and what to follow to return or destroy such data. Please remember a DUA may have descriptions of such requirement. The IRB may also request the ORPC perform a Post Approval Protocol Monitoring (PAPM) process to ensure these steps are taken. Please contact Stacy Cahill, UMBC Chief Information Security Officer, string1@umbc.edu, for additional information and guidance.
Have a Kuali technical issue or problems with access? Contact the ORPC on this online form and we’ll send your issue to VPR Research Administrative Systems
————————————
“Sensitive research data” is any information under UMBC control that is not “public information”, in physical or electronic format, that contains personal identifiers, UMBC proprietary information, sensitive research data, or data that is specifically controlled by laws or regulations. UMBC has a policy that classifies the difference between public information and sensitive information – see below. Research data can fall within any of these four levels, unless the research sponsor proscribes specific data protection requirements. Principal Investigators who plan to use such information are responsible for establishing the sensitivity level of their research data. These levels are summarized as:
Level 3
Information designated as sensitive by laws or regulations, such as medical records covered by the Health Information Portability and Accountability Act (HIPAA)
Level 2
Personally identifiable information collected and retained by UMBC about any member or affiliate of the UMBC community
Level 1
UMBC proprietary institutional information
Level 0
Public Information not classified as level 1-3.
————————————
What are the best devices to use for collecting, storing and analyzing data? This depends on the type of data – public information or highly sensitive files. Review DoIT’s guidance What Device Can I Use for UMBC Work as a Staff or Faculty Member?
————————————
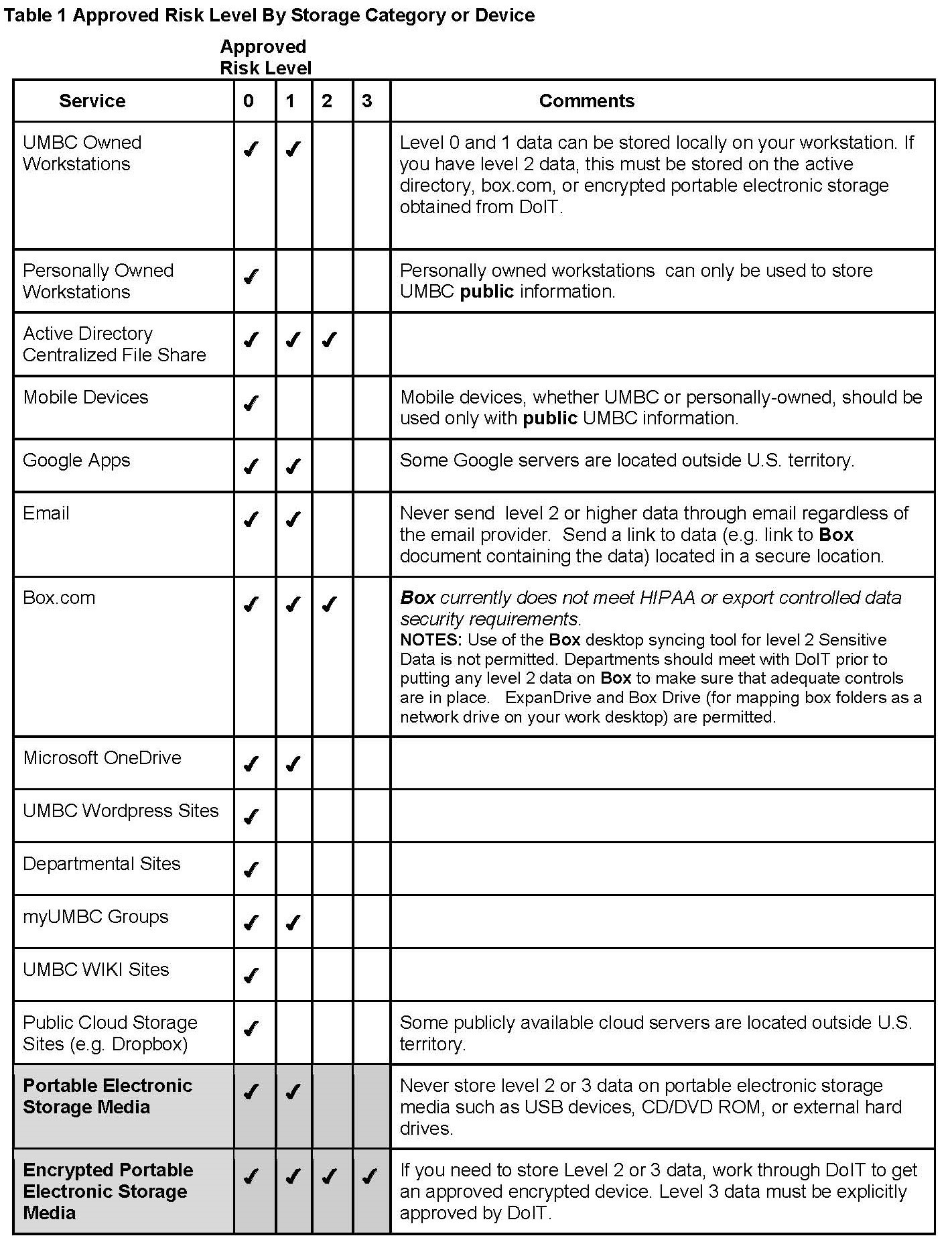
The DoIT table of approved risk level by storage category or device is found below. Investigators are advised to assess the security level of any service or application not listed in Table 1 before posting or storing sensitive information. If you have questions, please contact DoIT by submitting an RT request.